Securing What Matters MostSave Up To 35% With Our Annual Cybersecurity Plan
Our Clients


SERVICESExpert Cybersecurity Services
Ensure smooth operations and optimal performance with our comprehensive cybersecurity services.
We offer VAPT Services for Web, Mobile, Cloud, API, Thick Client, Infrastructure, and Wireless. Our team of best security analysts identify security issues in your assets and provide you a comprehensive detailed report.
We offer Red Teaming services to help you identify external and internal threats to your systems by simulating real world attacks to achieve the client’s defined objectives.
We offer Source Code Review Service to help you identify any security issues in your source. Our Source Code Review Service ensures confidentiality and integrity of your code focusing on traditional and logical security issues.
Conduct advance cybersecurity training programs for your employees and managers to spread awareness about latest cyberattacks, and precautions, to keep your business safe.
We can simulate real world attacks against your organization to test your effectiveness against a cyberattack.
Conduct an audit of your system configuration to identify insecure configurations, services, processes, applications, running in your system that can be an attack vector for a hacker.
We offer NIST 2.0 consulting services to help organizations smoothly implement NIST framework in their organization in a cost-effective and implementable manner.
Secure your Smart Contracts and Web3 applications with our Smart Contract Audit service. Our Web3 Analysts review your source code and perform logical test cases to identify security issues in your contract.
Monitor, Detect and Prevent cyber threats in real time. We offer Managed SOC services for all types of businesses to help them monitor and prevent cyber incidents in their organization.
CASE STUDIESComprehensive protection for your business
Our mission is to safeguard our clients digital assets through expert cybersecurity services and solutions.

“We work closely with our clients to ensure that their goals are met at every stage of the security assessment. We stay connected with our clients throughout their journey always helping them stay secure.”
WHY CHOOSE US?We always put in our complete efforts in every project to provide best results to our clients
Security Assessments
We always thoroughly check the application for all security test cases and issues ensuring that client applications and data are always protected from attacks.
Cost-effective and Implementable Solutions
We provide cost-effective and implementable solutions to our clients that align with their tech infrastructure. We put in efforts to study best mitigation strategy and provide the strategy to our clients.
Detailed Reports
Our reports are detailed, comprehensive and easy to understand allowing developer teams and IT managers easy understand the security issue and its corresponding mitigation.
Security Experts
Our security analysts are experts in their field. Each analysts has vivid skill set which has helped us build a strong team with all necessary skills for our clients. Our team continuously learns and keeps themselves updated to provide best results to our clients.
In The News
ToolsReal Tools. Real Penetration Testing. Real Impact and Enhanced Security.
Frequently Asked Questions
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security testing methodology designed to identify, evaluate, and mitigate vulnerabilities in a system, application, or network.
After a cyber attack, the first thing to do is disconnect any affected computers or devices from the internet to stop the attack from spreading. Then, check what was impacted and follow your plan for handling such incidents. It’s important to save any information that could help understand what happened, and fix the issue by using backups if needed. Inform everyone who needs to know, including customers and authorities if necessary. Once things are back to normal, review what went wrong and strengthen your security to prevent it from happening again.
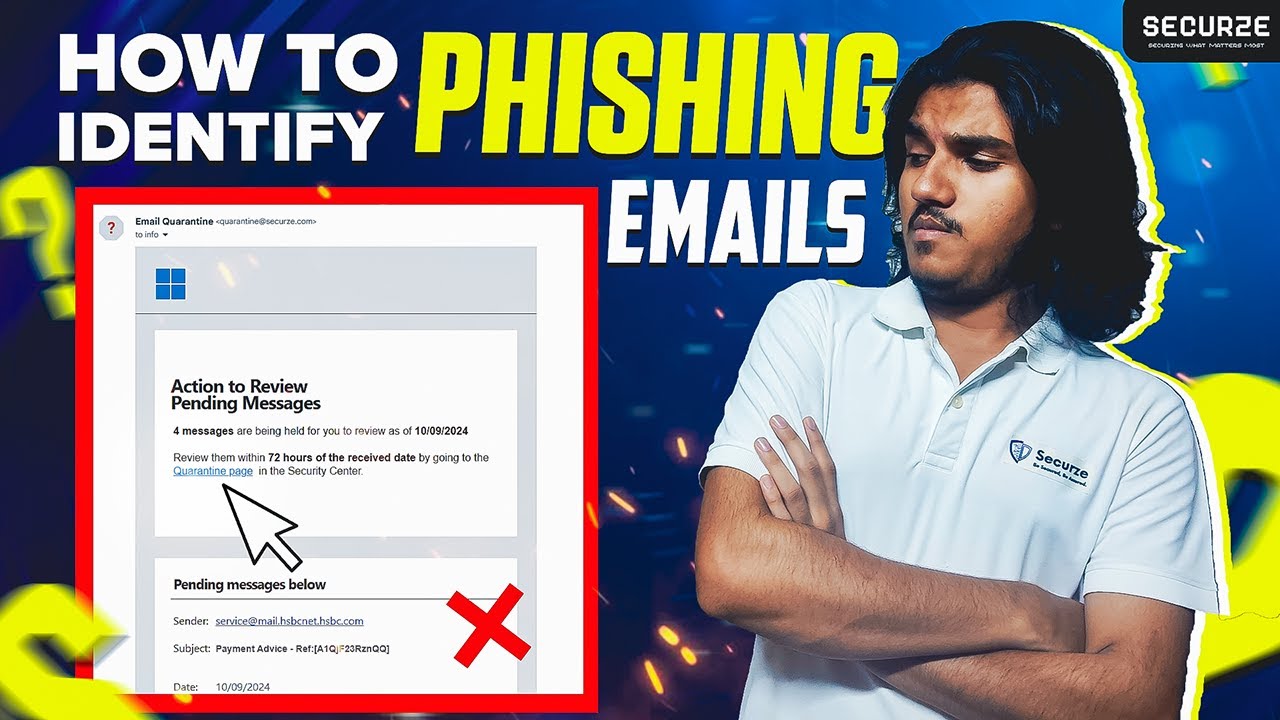
Common cybersecurity threats include phishing, where attackers send fraudulent emails or messages to trick users into revealing sensitive information such as passwords or financial data. Malware, including viruses, ransomware, and spyware, is another major threat, as it can infect systems, steal data, or cause significant damage. Ransomware specifically encrypts a victim’s data, demanding a ransom payment for its release. Denial of Service (DoS) attacks overwhelm systems or networks, rendering them unusable, while insider threats involve employees or trusted individuals misusing their access to steal or damage data. Additionally, zero-day vulnerabilities are exploited before a security patch is available, making systems vulnerable to attack.
Outsourcing cybersecurity services offers several key benefits to organizations. Firstly, it provides access to specialized expertise and advanced tools that may be difficult or costly to develop in-house, ensuring a higher level of protection. It also reduces the burden on internal teams, allowing businesses to focus on core operations while experts handle security monitoring, threat detection, and incident response. Outsourcing is often more cost-effective, as it eliminates the need for hiring, training, and maintaining a full-time cybersecurity staff. Additionally, outsourcing partners can provide 24/7 monitoring and faster response times to emerging threats, enhancing overall security posture. Finally, it ensures compliance with industry standards and regulations, helping to mitigate risks related to data breaches and legal liabilities.

CAREERSJoin Our Dynamic Team: Current Job Openings
If you have a passion for technology and a desire to make a difference in the world, a career in cybersecurity may be right for you.
Security Consultant
Security Operations Center
Keep your data secure!
Access to dedicated team of our best hackers and security professionals who do perfect solutions.